The Importance of Database Security: Establishing Rules and Roles for Your Clinical Study
by Vibeke Brinck | Jan 06, 2021 | Data Management | comments

Data security is paramount in your clinical research studies.
The National Institute of Health (NIH) requires airtight security when it comes to handling patient’s protected health information (PHI). Any study receiving funds from the NIH must have HIPAA (Health Care Portability and Accountability Act) and FDA 21 CFR Part 11 compliant solutions.
It is a serious issue to underestimate the importance of database integrity and security. Without the proper data security measures and oversight in place, the integrity of your data could be called into question.
So how can you ensure both your patient’s safety and privacy along with the credibility of your results?
A properly designed research database accomplishes this by establishing clear rules that protect and back up the data. Study-specific roles that set boundaries for users’ ability to access and edit the data is also a vital element of the data protection strategy.
When designing a database to collect, store, and produce the results of your clinical research study, be sure to consider and account for the following:
A secure and reliable system.
Only designate one user per login and make sure your system uses a secure authentication procedure for access. It is essential that all data is password protected and encrypted at all times, whether in use, transit, or storage.
Data request limitations.
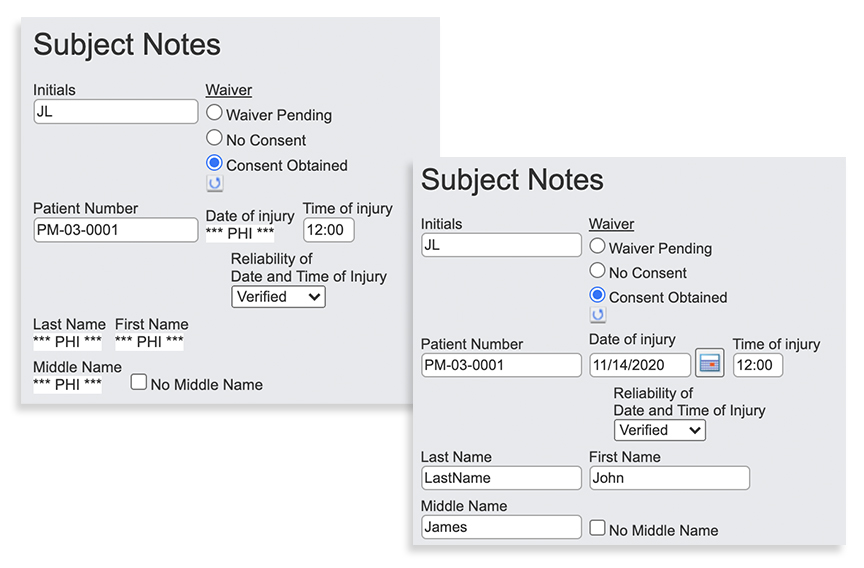
While some studies don’t involve a lot of personal information (PHI), most case report forms (CRFs) will include PHI like name, social security number, address, email, date of birth, etc.
Because of all the sensitive PHI included with clinical studies, investigators should work with a tool that allows specific fields to be marked as protected under HIPAA. Form-driven PHI protection will automatically create forms and outputs with PHI omitted or blocked out when the data is accessed and downloaded.
User permissions guidelines.
All studies will be unique. Some are small with a research assistant entering data. Others are more expansive with several geographically separate groups requiring access to view and enter data. Large studies will often have many medical specialties contributing to the research effort — sleep assessments, headache assessments, and neurocognitive assessments might all be different areas of one study.
Regardless of the size and scope of your clinical study, though, one of your first steps is to identify all involved parties and define who among them can and will input data and at what stages.
Guidelines for user access.
An auditor tasked with making sure the data is complete doesn’t need access to PHI. Similarly, investigators across multiple sites probably don’t need to see the data entered at other sites.

When too many users or the wrong people have access to too much information, severe patient privacy violations can occur.
For example, consider what could happen with an NCAA study of student-athletes.
If multiple schools are participating and could see each other’s results, it would be bad if a star quarterback for a Big 10 team is shown with a specific injury or ailment.
Ultimately, limiting access to who sees what within your clinical research study is essential in preserving participants’ privacy.
Don’t forget about dates.
It’s important to remember that every date included in a clinical trial database is PHI.
If the actual date of a specific medical appointment is included, it would be easy for someone to look up all patients who were seen in a specific location on that date and deduce the patient’s identity from there. Using a system that works with “time since injury” as opposed to specific dates can eliminate this potentially dangerous situation. 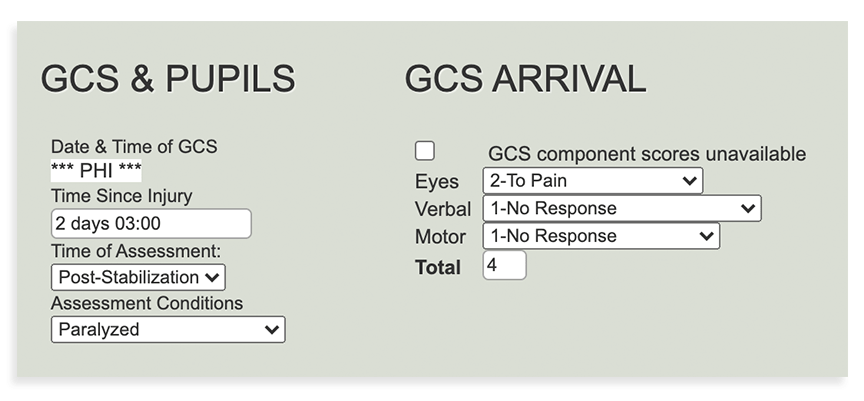
With this function, your research will only look at a baseline “date” for when an injury, appointment, event, etc., occurred — and work in subsequent time spans (i.e., 4 days after injury date, 14 days after injury date, and so on).
Always have audit trails.
As clinical studies progress and data is seen and accessed by various groups, red flags may arise from time to time. Maybe you notice during your audit that “John Doe” is listed as pregnant.
When things like that don’t add up, it’s important to be able to go back and see who entered the data, when they entered it, and if/when it was changed. If, upon further review, you determine “John Doe” is a female, then you’re okay. If not, going back through the audit trail to rectify the issue is essential.
Audit trails are not only an essential security function, it is an important accountability tool that ensures data integrity.
Finding the Right System for Your Brain Health Studies
The points listed above cover the key considerations for establishing rules and roles when setting up your research database. Even with superior technical know-how, there are many nuances that must be taken into account to guarantee HIPAA compliance.
- Who can see the data?
- Who can edit the data?
- When can they see and edit the data?
While you may have the answers, the complex variables that go into designing and setting up a database to accommodate everything can be complicated for many investigators.
For the past 15+ years, QuesGen Systems has been the leader in brain health clinical data management and research systems for academic and commercial studies — your partner in setting up and managing research projects with compliant, high-quality data that lets you focus solely on analysis of your game-changing results.

